 When you’re hosting your website and running your shack using your home network it’s important to keep an eye on the visitor traffic arriving at your site.
When you’re hosting your website and running your shack using your home network it’s important to keep an eye on the visitor traffic arriving at your site.
There’s a lot of useful info to be gathered by reading your server log files whether they’re your webserver logs or the connection log for your hotspot, mmdvm dashboard or repeater logs.
To begin with there’s the useful meta data such as browser and O/S info which will give you an insight into the software your visitors are using which can help with tailoring your website to work with different browsers and software or with identifying issues and problems.
But these posts are meant to give you a few ideas about maintaining your network integrity and security so first of all, you need to be reading the logs. Log files are usually just plain text files so all you need to read them is a simple text editor. You’ll also need to know where they are stored on your system, most MMDVM’s and many Webservers use a version of the Linux operating system and Linux uses a standardised file structure so for example, your MMDVM log files will probably be stored in /var/log/apache2/ if you’re using Pi-Star or WPSD on your hotspot and the file name will be access.log if you’re using a different system just google to find the location.
Once you have your log file open you will see a line by line breakdown of each request made by a visitor. First is the visitor’s IP address followed by the date and time of the request, this is followed by the type of request “GET” or “POST” for example and then comes the interesting bit which contains the filepath and requested file, the protocol and the code returned. This is followed by the user’s browser info and operating system versions as in this example of a request for the robots.txt file from the Apple search bot.
[27/Sep/2024:17:45:11 +0000] “GET /robots.txt HTTP/1.1” 301 162 “-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.4 Safari/605.1.15 (Applebot/0.1; +http://www.apple.com/go/applebot)”
So far so good, but let’s get to the ‘security’ bit and how log files can help identify threats to your system and attempts to exploit weaknesses.
The majority of threats to your system will generally be from malicious bots and not from some guy in a hoodie who is tapping in commands on a keyboard at the dead of night so let’s take a look at bot ‘hits’. Bot hits are easy to spot because they usually come as a block or flood of requests to the server. 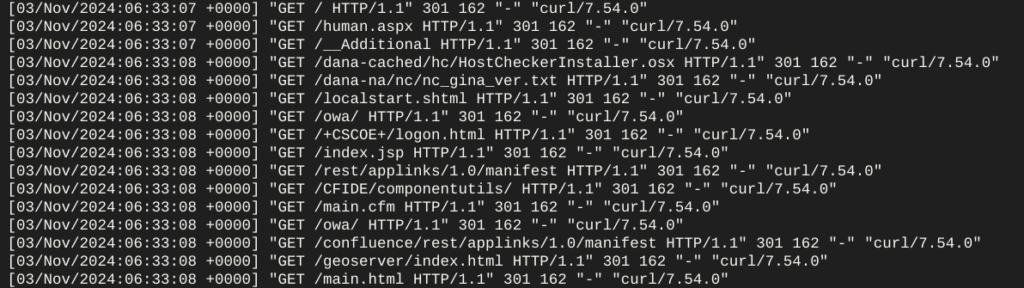
Like that. The bot in this case is trying to get a positive ‘hit’ from its list of vulnerable or exploitable resources using curl, it will compile and save a list of positive hits, recording the IP address of the server, if it doesn’t get a positive ‘hit’ it will move on and try the next IP on its list.
So your log file is now useful in two ways, firstly it can now provide you with a list of ‘exploitables’ to avoid using on your system/server and secondly it provides you with an attacker’s IP address which you can block using your system’s firewall.
(Expect more about firewalls later)
Meanwhile, one last tip for viewing log files. You can view your log file in real-time using a Terminal window, just open a terminal on your MMDVM or server and type:-
sudo tail -f /var/log/apache2/access.log
Have fun 🙂
 Yodabytz just added a Web Application Firewall script to his portfolio.
Yodabytz just added a Web Application Firewall script to his portfolio. My fave github coder has added another useful script to his portfolio.
My fave github coder has added another useful script to his portfolio. When you’re hosting your website and running your shack using your home network it’s important to keep an eye on the visitor traffic arriving at your site.
When you’re hosting your website and running your shack using your home network it’s important to keep an eye on the visitor traffic arriving at your site.
 So here you go, my Network Security Tip #1 for anyone with an Internet connection in the shack.
So here you go, my Network Security Tip #1 for anyone with an Internet connection in the shack. with cubesat and a homebrew circular polarised antenna.
with cubesat and a homebrew circular polarised antenna.
 Our new server is up and running and the Bromley Repeater Group Blog content has been reloaded from the backup.
Our new server is up and running and the Bromley Repeater Group Blog content has been reloaded from the backup.